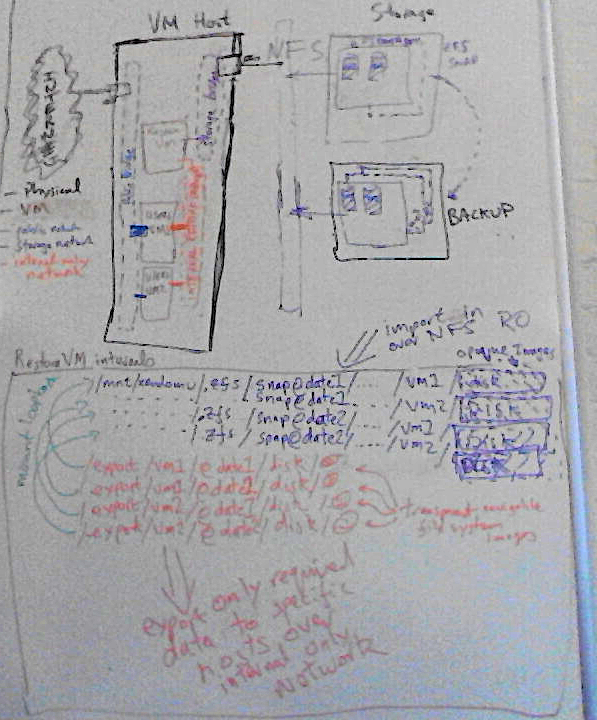
I have made some good progress on this, most of the work so far has gone into several Ansible roles:
Lots of things are still missing:
- Using MySQL passwords for SFTP.
- Email notifications on account creation.
- CMS installs.
- Log rotations, etc etc.
I have also hit a point at which a key decision needs to be made, I think we need to stick with Apache because so many applications that clients run depend on .htaccess files, we also need Apache to be configured so users can’t use it to read each others files, so we have a few choices:
ITK MPM
We currently use apache2-mpm-itk, it has a key disadvantage, it doesn’t support HTTP/2, but it has the advantage that it works with the existing user / directory layout we have on the Stretch and Jessie servers so would be simple to use on Buster.
suEXEC
The suEXEC module and the SuexecUserGroup Directive, the key problems with this is that we would have to have a directory layout like this:
\
`-- var
`-- www
|-- user1-site1
|-- user1-site2
|-- user2-site1
`-- user3-site1
With:
<VirtualHost *:80>
SuexecUserGroup user1 users1
ServerName user1.example.org
DocumentRoot "/var/www/user1-site1"
</VirtualHost>
<VirtualHost *:80>
SuexecUserGroup user1 users1
ServerName site2.example.org
DocumentRoot "/var/www/user1-site2"
</VirtualHost>
<VirtualHost *:80>
SuexecUserGroup user2 users2
ServerName user2.example.org
DocumentRoot "/var/www/user2-site1"
</VirtualHost>
As the documentation explains:
For security and efficiency reasons, all suEXEC requests must remain within either a top-level document root for virtual host requests… if you have four VirtualHosts configured, you would need to structure all of your VHosts’ document roots off of one main httpd document hierarchy to take advantage of suEXEC for VirtualHosts.
This could be combined with chrooting Apache and doing something clever with mounts?
Debian packages two versions of suEXEC, the upstream version and the custom version, the apache2-suexec-pristine package is complied with these options:
/usr/lib/apache2/suexec -V
-D AP_DOC_ROOT="/var/www"
-D AP_GID_MIN=100
-D AP_HTTPD_USER="www-data"
-D AP_LOG_EXEC="/var/log/apache2/suexec.log"
-D AP_SAFE_PATH="/usr/local/bin:/usr/bin:/bin"
-D AP_UID_MIN=100
-D AP_USERDIR_SUFFIX="public_html"
And the apache2-suexec-custom version with:
/usr/lib/apache2/suexec -V
-D SUEXEC_CONFIG_DIR=/etc/apache2/suexec/
-D AP_GID_MIN=100
-D AP_LOG_EXEC="/var/log/apache2/suexec.log"
-D AP_SAFE_PATH="/usr/local/bin:/usr/bin:/bin"
-D AP_UID_MIN=100
The default /etc/apache2/suexec/www-data file contains:
/var/www
public_html/cgi-bin
# The first two lines contain the suexec document root and the suexec userdir
# suffix. If one of them is disabled by prepending a # character, suexec will
# refuse the corresponding type of request.
# This config file is only used by the apache2-suexec-custom package. See the
# suexec man page included in the package for more details.
Apache per user
An Apache process per user, on high port numbers, running in a chroot, with a reverse proxy on ports 80 and 443?